Pentesting as a Service
CONTINUOUS SECURITY, REAL-TIME RESULTS
Identify vulnerabilities with real-time insights and rapid results. With the Penetration Testing as a Service (PTaaS), you don’t have to wait weeks for a final report – see vulnerabilities as they are discovered and take action immediately.
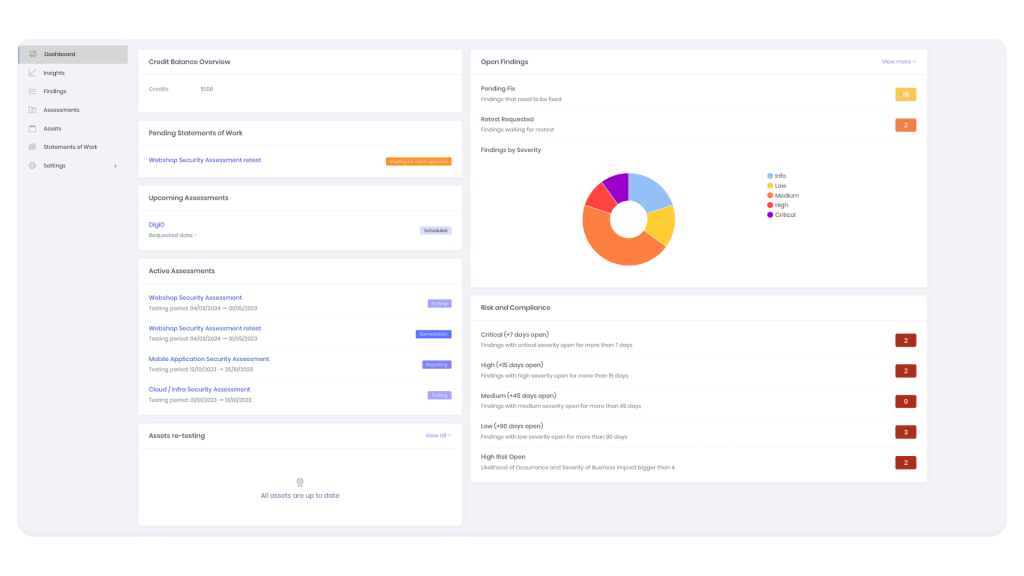
what is Pentesting?
A pentest, short for penetration test, is a simulated cyberattack performed by hackers to uncover vulnerabilities in your network, applications, or other digital assets. Unlike a vulnerability scan that only detects known issues, a pentest goes deeper—mimicking real-world attacks to identify weak points, including those unknown to your team. With Penetration Testing as a Service powered by Hacksclusive, you get fast, actionable results through a cutting-edge platform, empowering you to secure your systems proactively.

TRADITIONAL PENTESTING REIMAGINED
Traditional pentests take up to six weeks before you see results. With PTaaS, you get the first findings within a week, enabling you to fix vulnerabilities before they can be exploited. Our platform facilitates seamless collaboration between your internal security team and expert ethical hackers, ensuring faster remediation.
WHY CHOOSE PENTESTING POWERED BY HACKSclusive?
Real-time insights
Detect vulnerabilities sooner. Access live updates on vulnerabilities found during the pentest instead of waiting for a final report. The platform keeps you informed with real-time data, enabling faster responses and more effective security measures.
Collaboration across teams
Security isn’t just for CISOs. The platform is designed for all stakeholders – from security engineers and developers to CIOs and product owners. Internal teams and external hackers can collaborate in one shared space, streamlining communication and remediation efforts.
Integration
Easy manage the mitigation of vulnerabilities with integration with tools like Jira.
Faster remediation
By having instant access to vulnerability reports, your team can begin fixing issues right away, reducing the window of exposure to potential cyber threats.
Multiple tests, one platform
For organizations with multiple applications, our platform allows you to run several penetration tests simultaneously, optimizing efficiency without compromising security quality.
More than just a vulnerability scan
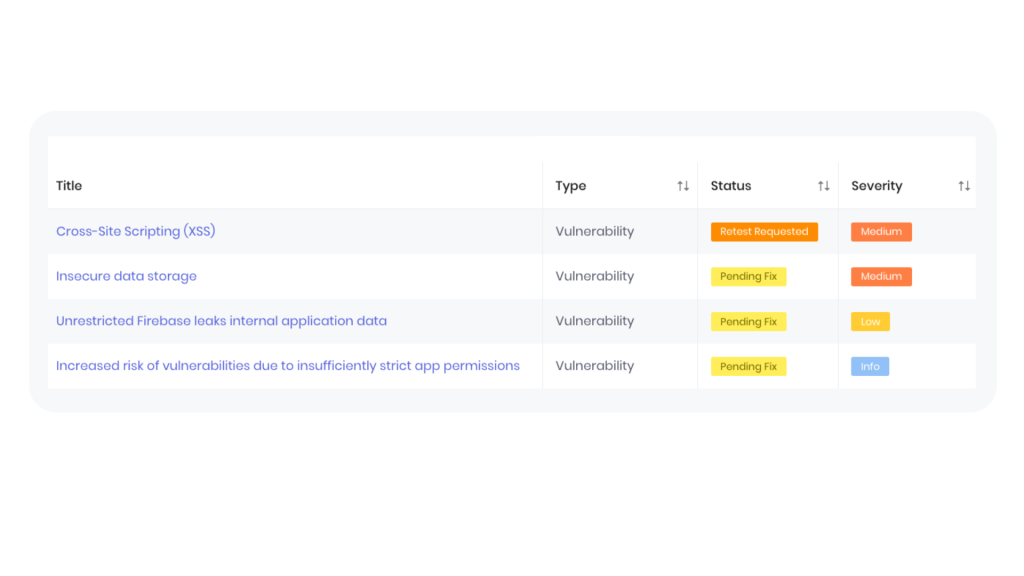
A vulnerability scan detects known threats, but a pentest goes deeper, simulating real-world attacks to uncover unknown security gaps. Ranging from black to white box assessments, our experienced ethical hackers use advanced techniques to identify and exploit weaknesses, providing you with a comprehensive security assessment.
FULL-SCOPE SECURITY TESTING
Our pentesting services cover
- Design & configuration assessments
- Code reviews
- Web & mobile application security testing
- Infrastructure & network assessments
- Device assessments (“hardware hacking”)
- Hands-on manual penetration testing
- Red teaming for advanced attack simulations
Shop more products

Pentest
A Pentest is a hands-on security assessment designed to uncover vulnerabilities in your digital environment. Delivered through the Hacksclusive platform, it gives you real-time results and clear next steps.
Bug Bounty
A Bug Bounty is a “no cure, no pay” program in which Zerocopter hackers are invited to look for any vulnerabilities in your environment. Matching you to the best hackers for your scope, and triaging all the incoming reports, it offers a continuous way to test your system.
Coordinated Vulnerability Disclosure
Show to the world that you are open to receive vulnerability reports from the hacker network, while also prioritising what matters most. Have your CVD managed to receive only the valid and relevant reports.
Dedicated Hacker Time
Dedicated Hacker Time gives you instant access to your extended team of hackers on an hourly basis. Zerocopter will match the best hacker(s) to your specific security concerns, whether it is just an hour of advice or a full test of your systems or applications.
Recon
Harness the expertise of the Zerocopter hacker network for 10 hours, conducting thorough assessments of your public-facing assets that might have previously gone unnoticed and, more importantly, unsecured.
